Sunday, Sept 22 2024
Fishing for hackers: Analysis of Linux Server Attack
By A Mystery Man Writer

Most Common Hacking Techniques

Malicious Input: How Hackers Use Shellcode

What is Phishing Attack in Cyber Security - Complete Guide

Zphisher - Automated Phishing Tool in Kali Linux - GeeksforGeeks

Blog hackers-arise
6 Types of Database Hacks Use to Obtain Unauthorized Access
Make your First Malware Honeypot in Under 20 Minutes
phishing-attacks · GitHub Topics · GitHub

Fishing for hackers: Analysis of Linux Server Attack

HHS - Lesson 7 - Attack Analysis - Hacker Highschool
How to Extract Memory Information to Spot Linux Malware
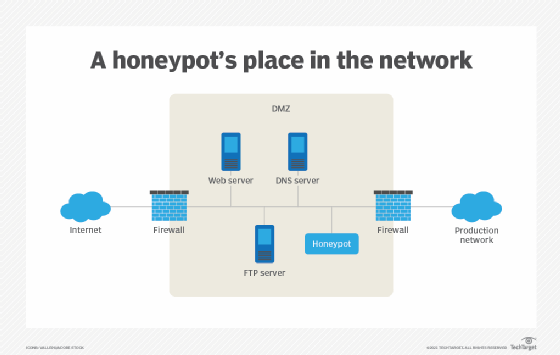
What is a honeypot? How it protects against cyber attacks
Related searches
- Cyber Thief Hacker Holding Fishing Rod Stock Vector (Royalty Free) 618026720

- A cyber thief is stealing password with fishing rod from the

- Masked robber with a fishing rode stealing - Stock Illustration

- Fishing spots, fishing reports and regulations in Hacker Brook
- Savage Gear Bait for Ocean Fishing 13 cm 73 g Cast Hacker Fast Sinking

Related searches
©2016-2024, caddcares.com, Inc. or its affiliates
/0x2nh0m95kqe5dmq3day92jsphdg)


